Real-time visibility into software risk and compliance.


















Why TripleKey Exists
Healthcare software guides life-critical decisions, yet software risk remains invisible until it’s too late. We built TripleKey to close that gap.
Health Systems
Healthcare Partners
Choose Your Path
TripleKey was built for healthcare systems and healthcare partners.
.png)
Health Systems
.png)
Healthcare Partners
Continuous Insights.
Healthcare innovation shouldn't be a liability. TripleKey provides continuous, forensic-level visibility into software risk, security, and code provenance—all within a single platform that protects your partner relationships while accelerating your digital roadmap.
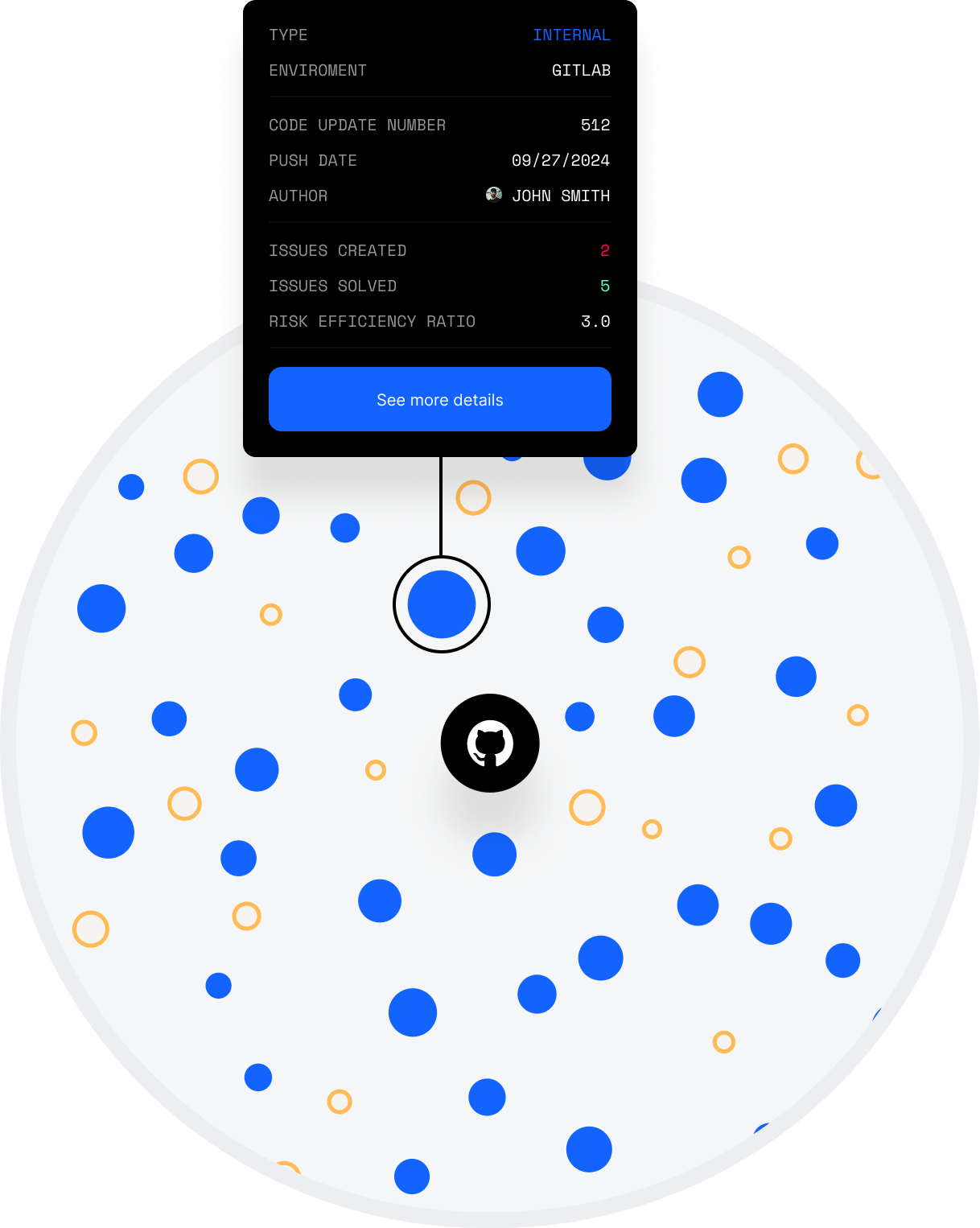
Software and Code Health

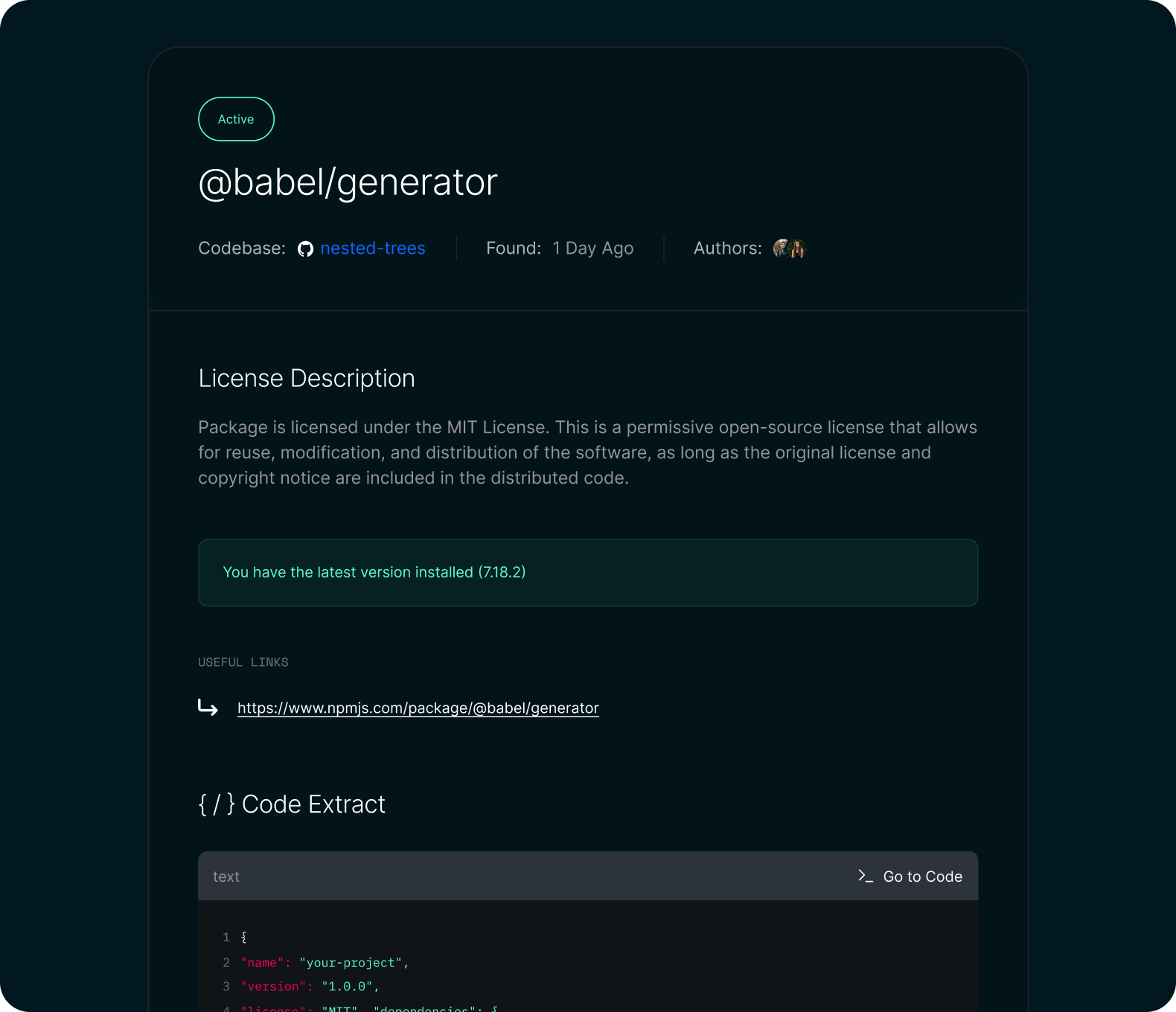
Intellectual Property & License Compliance
Contributor Risk & Code Provenance
Built for Healthcare Decision Makers
Clear insight for every stakeholder—without technical overload.
Visibility into healthcare software risk
Gain continuous insight into security posture, code health, and vendor-delivered software

Executive-ready insight without technical noise
Understand software risk, vendor exposure, and contributor risk at a strategic level—so decisions are confident, timely, and defensible.

ROI-driven visibility into software and vendor risk
Connect engineering and vendor spend to measurable outcomes. Forecast risk, justify investment, and support compliance with transparent metrics.

Continuous due diligence for healthcare software
Move beyond static diligence reports. Gain ongoing, independent visibility into software quality, compliance posture, and execution risk.







